Data Protection Checklist

Modern Data Protection Checklist
DataPivot provides customers a checklist to help evaluate their backup/recovery software requirements and find the best technology fit. This list has been created by DataPivot engineers using best practices garnered from years of designing, implementing and supporting backup and recovery solutions of all types.
Backup Software Requirements Checklist
What Does Success Look Like With a New Backup Solution?
A good process when evaluating global backup is to start with a blank sheet of paper and brainstorm what you want in a solution.
-
Define your requirements and goals, avoid letting vendors tell you that you should do or let your existing investments compromised what you really want to do
-
Gather up a comprehensive list of reasons of WHY or business drivers of WHY you’re doing the project and going to spend or invest money to make a change.
-
List areas where current solution is falling short of objectives, isn’t meeting requirements, or doesn’t have the attributes you want. (Examples include: complexity of supporting multiple backup applications, spiraling storage costs, support is being dropped, new workloads not supported, legacy workloads not supported, NAS backups)
-
List what attributes you want in a solution (non-technical)? Examples – Unified, Global, automated, reliable, easy, consolidated, versatile, self-service, open, software defined, user experience, insight/visibility, cost-effective, comprehensive.
-
Do you prefer a SaaS based solution or a software defined solution running on-premise or in the cloud?
-
Define what project success looks like.
Examples of Requirements
Comprehensiveness of the solution and Track Record of the vendor
-
One Single Global Backup & Recovery/Modern Data Management solution is desired. (Ex. Currently there are multiple point products that are not seamlessly integrated which limits flexibility and makes reporting/insight and DR challenging).
-
R&D and innovation investment by the vendor
-
Global references at scale. What Fortune 1000 Companies are using this product as an enterprise-wide standard?
-
Gartner Magic Quadrant and other analyst rankings
-
High quality enterprise support model
-
Quality Global Reporting.
-
Scalability – How does the solution scale? Can it scale efficiently? What’s the hardware footprint to scale?
Technical Capabilities
-
Database integration – MS SQL, Oracle, DB2, MariaDB, PostgreSQL (List Databases the solution supports)
-
Support for Physical servers
-
Support for Hypervisors (list all)
-
NAS backups
-
Support for Operating Systems (list OS’s)
-
Snapshot Integration and Orchestration with major SAN and NAS vendors
-
Native Public Cloud Integration (Amazon, Azure, GCP)
-
Ability to write data deduplicated and encrypted to major public clouds.
-
Backup from on premise to cloud or vice-versa.
-
Support for IaaS instances.
-
Support for Cloud database service backups.
-
Support for containers (Kubernetes)
-
-
Support for SaaS applications (M365/Salesforce/Google Workspace) and endpoints
-
Enterprise Scheduling
-
Built-In Workflow Engine
-
Database refresh capability for Dev/Test/DR (Copy Data Management)
-
Live Browse, Refresh, or Mount Capability from Snaps
-
Active Directory full and granular restore capability.
-
AzureAD support
-
-
Does the software solution offer enterprise grade deduplication? (Software defined or hardware bound? Source Based or Target Dedupe)?
-
Bare Metal Restore
-
Physical to virtual or restore capability to a different hypervisor
Requirements Specific to Your Environment
-
Is the solution Software Defined or Appliance based or SaaS
-
Cost/Total Cost of Ownership Equation. Licensing Model – CAPEX, OPEX
-
GDPR and other compliance regulations
-
Cybersecurity Insurance Requirements (e.g. Immutability/Air Gap)
-
Define RPO or RTO for DR scenarios
-
Ability to support multiple retention policies
-
Encryption requirements and support
Security
-
Ransomware Protection
-
File Anomaly Detection
-
Honeypots
-
Air Gap (support for tape/cloud)
-
Immutable storage support
-
-
Storage locks
-
Role based access control
-
Four eyes/multiple approvers for workflows
-
Automated DR testing
On-going Support (Vendor and Solutions Provider)
-
Solution must be easy to operationalize and have excellent support once implemented
-
Enterprise Services, Consulting Offerings for Implementation and on-going support
-
Monthly/Quarterly Health Checks and Long Term Project Assurance
DataPivot’s Ransomware Readiness Checklist for Enterprise Backup Software
DataPivot has developed a 12 Point Checklist for organizations to use to ensure their backup environment is optimized to mitigate the risks of Ransomware. Many – if not most – of these checkpoints are applicable to all backup software products.
-
Review Backup Server (Master Server) config
-
Ensure it is being backed up offsite and secure
-
Option: Failover with replication
-
-
What version of the software are you running? Recent? Supported?
-
-
Review Backup Software’s Security Assessment Report
-
If the software has a security dashboard, this is a valuable tool to leverage
-
Review the security dashboard (red, yellow, green)
-
Is your environment “hardened” with best practices
-
Are the necessary reports enabled?
-
-
Authentication Controls
-
Review Authentication Controls (LDAP, local accounts, Okta, Duo, AzureAD, CyberArk, e.g.)
-
Review MFA, if in place
-
-
Role Based Access
-
Review who has admin rights (Think about setting up accounts without delete rights)
-
Confirm alerts are set up when Admin account logged in/create
-
Rend: Disable admin rights (utilize least privilege)
-
-
Storage Locks
-
Review who has rights to delete storage policies
-
If software has Workflows, review these to prevent deletions, implement handshakes with two keys, set up alerts
-
-
Audit Logs
-
Review retention. Default is 365 days.
-
Different retentions for critical data
-
-
Encryption
-
Review what – if any – encryption is in place for data at rest and transit
-
Evaluate backup software’s encryption vs application vs hardware
-
Take note: Encryption can impact de-dupe and storage sizing
-
-
Ransomware Protection on Media Agents (Data Movers)
-
Does the software have Ransomware protection alerting? Is this enabled?
-
If the software supports the creation of Honeypots on Media Agents, test that alerts sent and backups are disabled
-
-
File Anomaly Detection
-
If the backup application supports File Anomaly Detection, is this enabled
-
Test alerts – confirm emails
-
This feature can help determine the “last good backup” before infection
-
-
Immutable Storage Options
-
Is immutable a requirement
-
An organization’s compliance department often defines this requirement (or not)
-
Cloud or On-prem options
-
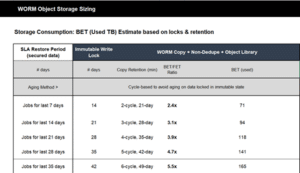
Sizing considerations and what needs to be immutable (not all data created equal) Immutability means the data cannot be deleted – even if you change your mind or policies. Immutability will impact your storage usage (more will be required, see DataPivot sizing sheet below)
-
-
-
Design and Workload Considerations
-
One-Way Firewalls (see Diagram below) and other hardening techniques
-
Airgap (Tape)
-
Backup to the Cloud
-
M365/Google Workspace Backups
-
-
Documentation
-
A backup and DR solution needs documentation (such as a run book) with screen shots
-
Know your support information
-
Who to call, Contract info
-
Test and Test again
-
Sample Inventory Spreadsheets and Checklists
Below are examples of a Spreadsheet Checklists that customers can use to take inventory of their environment and develop their requirements. These are available from DataPivot upon request.
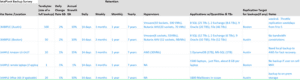
Here’s another, more detailed example:
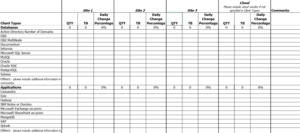
Below is a spreadsheet for sizing Immutable Storage:
Next steps
If your organization is thinking of replacing its existing backup software – or interested in a third-party evaluation of your current solution – please contact DataPivot for an introductory session. We can provide the materials referenced in this document and have an independent, objective technical discussion with our team of Data Protection experts.
DataPivot Contact Information: